Security Testing vs. Penetration Testing – Which One Should You Choose?
 KiwiQA
KiwiQAAcross the globe, there is an exponential increase in adoption of mobile phones and the internet. The phenomenon is no longer limited to developed nations, but paved waves into developing nations as well. Let’s take the case of a developing country like India where the mobile internet user base is expected to reach 1.5 billion[1] by 2040.
However, internet consumers need to keep the old adage ‘With great power comes great responsibility’ in mind when browsing on the internet. This is because cyber-attacks, data breaches, and other such incidents are on a continuous rise. Even experienced internet users fall prey to cyber-attacks!
As per reports, close to 92 percent[2] of the data breaches in the first quarter (Q1) of 2022 is due to cyber-attacks. The onus of minimizing the probability of data breaches and cyber-attacks also lies in the hands of enterprises whose apps (or websites) are used by their customers.
This is where enterprises can lean on security testing to make their products more robust and secure from a customer’s point of view. In this blog, we will cover the integral aspects of security testing, along with deep diving into penetration testing (which is also a form of security testing). We will also touch base on the key differences between security tests and penetration tests.
So, let’s get started…
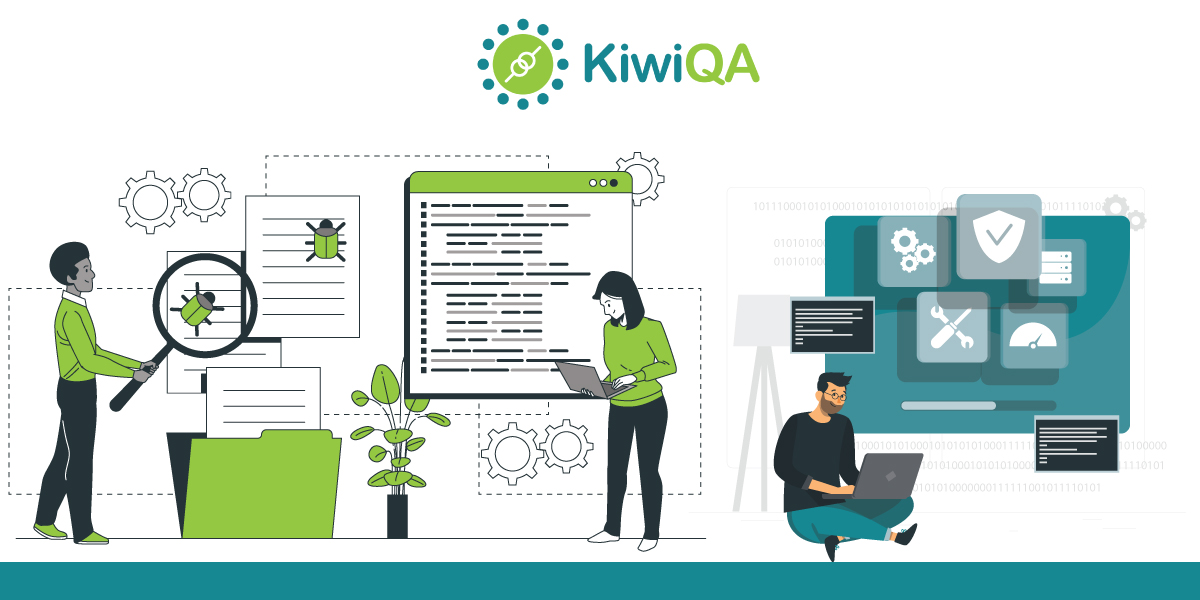
As the name indicates, security testing is a broad term that encompasses the tests conducted for detecting the vulnerabilities in the product. Security tests are conducted to detect vulnerabilities in the network, product, and the physical environment.
Since there are threats of data getting leaked (or stolen) when it is in transit, it becomes essential to ensure that data security aspects are met whether the data is at rest or in transit. Security tests help in minimizing the risks of data thefts, network thefts, cyber attacks, and other forms of online attacks.
Since no product can go live without adequate security testing, it is recommended to partner with a security testing services company. This approach is particularly recommended in case there are no experienced resources well versed with security testing.
Also Read – Mobile App Security Testing Checklist
Mentioned below are the major forms (or types) of security testing:
In this form of security testing, the team members don the hat of a real attacker. The members receive every piece of information regarding internal structuring of the system. The security tests are based on the request-response mechanism.
Akin to black box security testing, here also the testers have every detail about the internal structure of the system. However, the tests are performed at the implementation level and testers check whether the existing implementation is aligned to the security requirements.
This form of security testing is an amalgamation of black box and white box security testing. The testers who perform grey box security tests do not have complete understanding of the code structure.
Instead, they are provided with the login credentials to identify the potential damage that a malicious actor can do if (s)he has access to the product.
For starters, penetration testing (or pen testing) is also a form of security testing where cyber-security experts try to exploit the security vulnerabilities in the system.
Zed Attack Proxy, sqlmap, Hashcat, Wireshark, nmap, Hydra, and Burp Suite are some of the most prominent penetration testing tools. The intent of running pentests is to build a more secure end product by unearthing the security vulnerabilities present in the system.
As mentioned earlier penetration testing is an integral type of security testing. Ethical hacking, network scanning, and vulnerability scanning are some of the other major types of security testing. In the interest of time, we would not deep dive into each & every type of security testing.
Also Read – Best Practices for Mobile App Penetration Testing
In penetration testing, pen testers identify the security vulnerabilities in the product; along with prioritizing the vulnerabilities based on their impact. If pentesting is also a type of security testing, how different is it from the other forms of security testing?
Let’s look at the differences in this section…
1. Security testing comprises different types – vulnerabilities scanning, API security testing, web application security testing, configuration scanning, and pentesting.
On the other hand, penetration testing (or pentesting) is a specialized form of security testing.
2. In security testing (barring aside pentesting), testers do not exploit the security vulnerabilities. Due to this, they do have any detailed guide on how to fix the issues.
On other hand, testers performing penetration testing always exploit the security vulnerabilities and provide a detailed fixation guide.
Also Read – Reasons Why Penetration Testing Is Important
3. As far as time duration for running tests is concerned, penetration tests take significantly longer than other forms of security testing. The test execution duration can vary from a few hours to days. This is because vulnerabilities have to be exploited in the system.
On other hand, security tests like vulnerability scanning can take around 20 minutes to 60 minutes.
4. Companies dealing with a large amount of sensitive data generally opt for penetration testing.
On the other hand, companies opt for other forms of security tests when they have to just perform security audits at a surface level. Since data has become an integral part of every business, it is recommended to consider penetration testing on priority.
Onboarding an experienced security testing company can be helpful in expediting the security and pentesting process.
If pentesting is so critical, the million $ question is which businesses should not skip penetration testing at any cost?
Penetration testing constitutes of different phases namely:
Refer the Infographic from KiwiQA that deep dives into the various phases of penetration testing:
5 stages of Penetration Testing from KiwiQA
Though penetration testing is essential for businesses that deal with a large amount of data, it is recommended for the following industries:
Security testing is an integral part of the entire software testing cycle. Since there are different types of security tests, it is important to choose the one that suits your requirements.
Penetration testing (or pentesting) must be considered on priority, especially if the project has to adhere to standards like PCI DSS, HIPAA, etc. To summarize, security testing and pentesting are recommended to be performed for any type of web project.
Subscribe to our newsletter for some hand-picked insights and trends! Join our community and be the first to know about what's exciting in software testing.
Welcome to the testing tales that explore the depths of software quality assurance. Find valuable insights, industry trends, and best practices for professionals and enthusiasts.

Fill out and submit the form below, we will get back to you with a plan.
 CRN:
22318-Q15-001
CRN:
22318-Q15-001 CRN:22318-ISN-001
CRN:22318-ISN-001 CRN:22318-IST-001
CRN:22318-IST-001